The Magnus Team regularly attend industry events and are looking to network with both the GovCon community / industry and government to discuss solutions and innovative approaches. Below are events where we have led engagements to collaborate with our government partners to discuss important topics.
.

2023 Homeland Security Conference – July 18-19, 2023
Today’s infrastructure is connected to many other infrastructure assets, systems, and networks for normal day-to-day operations. These connections may be geographically limited or dispersed over great distances. The many points of infrastructure connections and their geographic distribution can make the infrastructure environment much more complex.
The U.S. Department of Homeland Security (DHS) works to strengthen critical infrastructure security and resilience by generating greater understanding and action across a partnership landscape. This is achieved by working with private and public infrastructure stakeholders to resolve infrastructure security and resilience knowledge gaps, inform infrastructure risk management decisions, identify resilience-building opportunities and strategies, and improve information sharing among stakeholders through a collaborative partnership approach. The Cybersecurity and Infrastructure Security Agency (CISA) leads the effort to enhance the resilience of the nation’s physical and cyber infrastructure by bringing resources to your fingertips. Only working together can we defend against today’s threats and collaborate to build secure and resilient infrastructure for the future.
.
Thought leadership panels on Innovative Acquisition , Supply Chain Cybersecurity and Smart City / Connected Communities:



.

TechNet Cyber Conference 2023 (May 2-4 2023)
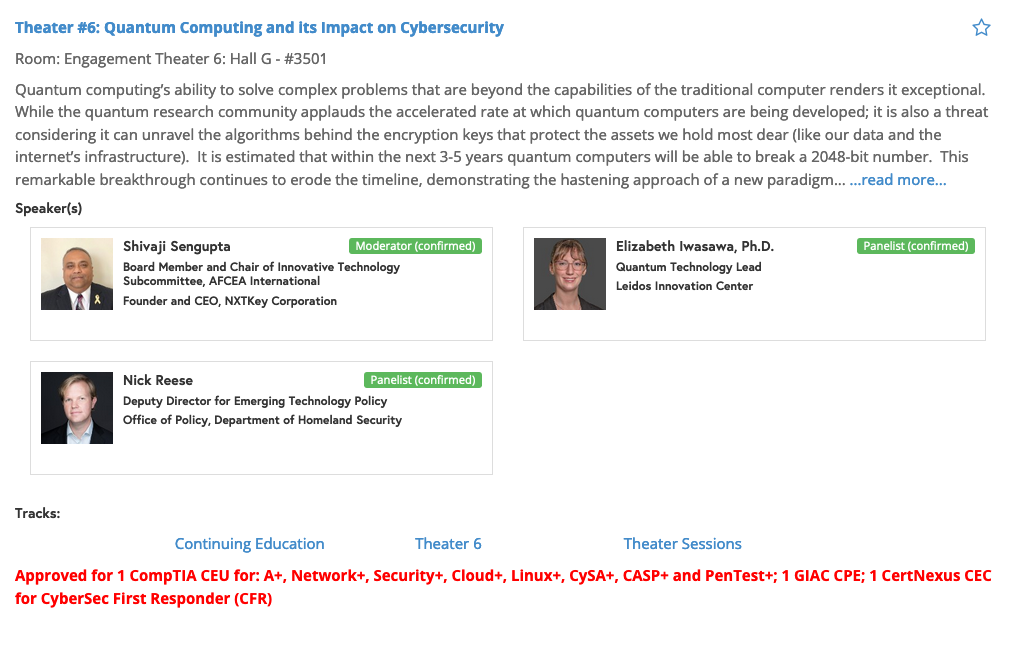
The harnessing of the right cyber power is more important than ever in a domain deluged by persistent attacks and simultaneous sophisticated campaigns that threaten global political, economic and security interests. Quantum computing’s ability to solve complex problems that are beyond the capabilities of the traditional computer renders it exceptional. While the quantum research community applauds the accelerated rate at which quantum computers are being developed; it is also a threat considering it can unravel the algorithms behind the encryption keys that protect the assets we hold most dear (like our data and the internet’s infrastructure). It is estimated that within the next 3-5 years quantum computers will be able to break a 2048-bit number. This remarkable breakthrough continues to erode the timeline, demonstrating the hastening approach of a new paradigm in security.
.
Quantum Computing and its Impact on Cybersecurity – May 3, 2023

.

The Federal Identity Forum (FedID) has been the U.S. Government’s annual identity conference since 1995. Its mission is to bring together identity experts to exchange information and enhance public-private collaboration to solve the federal government’s toughest identity challenges and help ensure a vibrant identity community. Shivaji Sengupta will be speaking and organizing the below panel discussions.
.
Wednesday 7 September 2022
11.30 AM – Panel on Supply Chain Cybersecurity and CMMC

Description
When folks think about cybersecurity, they most often think of securing their networks, software, and digital assets against cyber-attacks and data breaches. But the supply chain – whether a traditional manufacturer or service provider’s supply chain or the “data supply chain” relied on by most companies is also vulnerable to security risks, as has been seen in a litany of major data breaches via third parties.
The concept of supply chain is associated with the ability to effectively orchestrate multiple vendors to deliver a final product or service. The complementary adoptions of low-cost interoperable technologies, alongside rapid innovations in physical and virtual systems/applications, now comprise the core risk drivers of today’s public and private sector supply chains. Every company large and small in the DIB has a place in the supply chain, and supply chains are evolving to be as much about the flow of information as they are about the flow of goods and services.
As part of this panel, we are looking to address some key concerns like:
- Will CMMC limit the risks of the information supply chain?
- Will CMMC protect the Cyber Supply Chain it can’t see?
- How to address the Software Bill of Materials (SBOM) listed in the EOP?
.
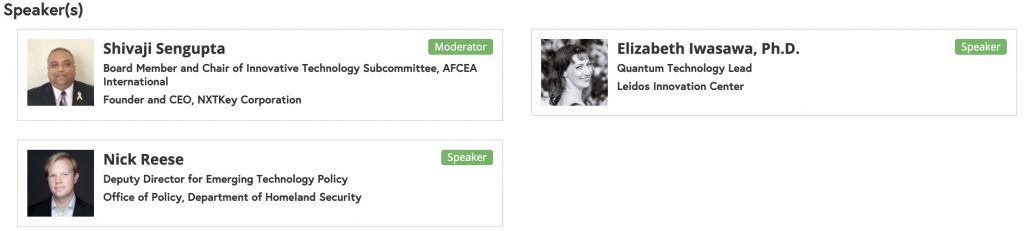
3.00 PM – Quantum Computing and its Impact on Cybersecurity
Description
Quantum computing’s ability to solve complex problems that are beyond the capabilities of the traditional computer renders it exceptional. While the quantum research community applauds the accelerated rate at which quantum computers are being developed; it is also a threat considering it can unravel the algorithms behind the encryption keys that protect the assets we hold most dear (like our data and the internet’s infrastructure). It is estimated that within the next 3-5 years quantum computers will be able to break a 2048-bit number. This remarkable breakthrough continues to erode the timeline, demonstrating the hastening approach of a new paradigm in security.
It is inevitable that threats will accompany this paradigm shift, it is also worth understanding what that threat might look like in reality and where will it come from. While much research still needs to take place, it is certain that the greatest risk will come from the data that must retain its secrecy well into the future. The data being referred to includes National Security Data, Banking Data, PII data, Health data, Intellectual Property, etc. This panel will outline challenges and solutions impacting the Government and industry related to quantum computing.
.
Thursday 8 September 2022
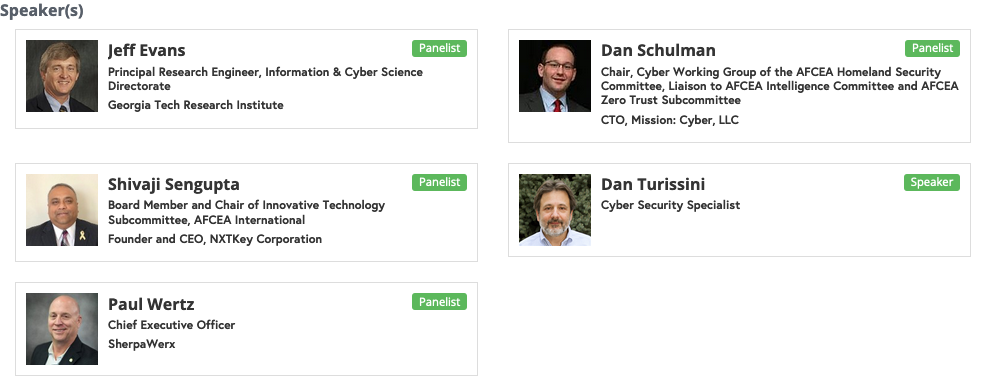
2.00 PM – Building Blocks for Cybersecurity Maturity and Opportunities to Help Protect the USA Supply Chain
.
Over the past 20 plus years Information Security, Information Assurance and now Cyber Security have increasingly become an exercise in managing risk to the point of almost abandoOver the past 20 plus years Information Security, Information Assurance and now Cyber Security have increasingly become an exercise in managing risk to the point of almost abandoning mitigating vulnerabilities. Relying organizations & consulting professionals have focused on using legacy techniques & stacking redundant symmetric authentication factors to avoid meaningful change. Security by obscurity, that has failed in the past, has once again become good enough to satisfy risk management objectives. The result is that we continue to conduct business online without confidence that the online credentials being used are accurately associated with a specific entity. We still offer little or no mechanism to confidently know the difference between legitimate & illegitimate parties/ entities transacting – while agreeing that they are the largest vulnerability. “On the Internet, nobody knows you’re a dog”, [Peter Steiner has been reproduced from page 61 of July 5, 1993 issue of The New Yorker, (Vol.69 (LXIX) no. 20) only for academic discussion, evaluation, research and complies with the copyright law of the United States as defined and stipulated under Title 17 U. S. Code].
The DoD is implementing a Cybersecurity Maturity Model Certification (CMMC) that offers a consistent roadmap for the Defense Industrial Base (DIB), and beyond, to mature its overall Cybersecurity capabilities in a proactive way in order to enhance their business case, protect their brand, while protecting our Nation’s Economy and Security. This session will challenge the .gov community at large and the and its associated supply chain to “move forward” by embracing the CMMC model and provide some incremental actions that can be taken to make this journey and integrated business initiative. This is particularly important doing business under a lowest price technically acceptable source selection process. The presentation will provide an overview of CMMC, how it puts a better focus on existing FAR requirements and provide guidance, particularly for Small and Medium size businesses that desire to do, or continue to do, business with the Federal Government. It addresses public companies that will need guidance to meet the growing SEC requirements related to Cyber Security Governance. The presentation will also introduce educational initiatives AFCEA is pursuing to achieve a Cyber Secure ecosystem.
.

AFCEA TechNet Cyber 2022 – April 26-28, 2022 • Baltimore Convention Center

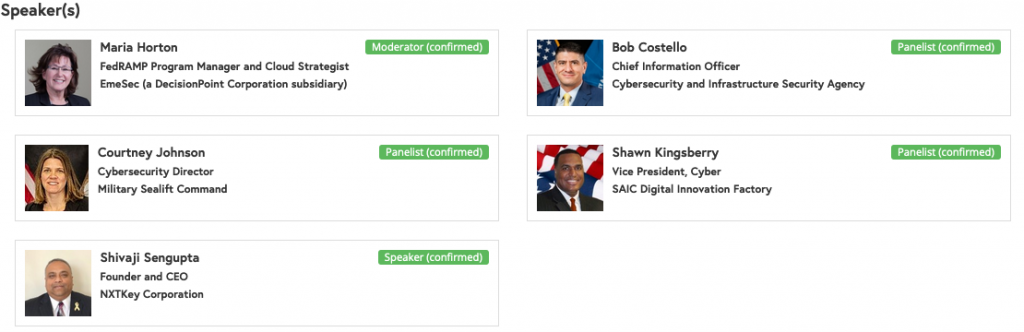
Supply Chain Cybersecurity is increasingly cited in regulations, legislation, and the news. This panel will explore and discuss the evolving implications and impact on Federal Contracting businesses. The questions will include operational and corporate strategies and tactics for managing supply chain in today’s world.
Supply Chain White Paper can be downloaded from here.
.

AFCEA NOVA Small Business Enterprise IT Day 2022 – May 5, 2022, 8:00 AM – 5:30 PM
Shivaji had the pleasure of attending the TechNet conference in Baltimore where we heard Gen Skinner outlining DISA’s mission to move at the “velocity of action to win”.
Entwined as part of that mission is the Strategic plan to sharpen DISA’s mission across a key line of effort which is “Leverage data as a center of gravity”.
We all know “Data is a vital strategic asset and a key enabler to C2”. Which was highlighted by Gen Skinner when he said “If you own the data – you will own the high ground at the end of the day.”
With that, Shivaji introduced Ms. Kuharske – Chief Data Officer at DISA for the fireside chat.
.






